What Is a DDoS Attack and How Does a DDoS Attack Work?
September 22, 2022 | By Admin

What Is a DDoS Attack (Distributed Denial of Service Attack)?
A DDoS Attack is a short form of distributed denial-of-service (DDoS) attack. In DDoS attacks, multiple compromised computers target a website, server, or other network resources through a flood of message requests or connection requests, or malformed packets.
DDoS attacks lead to a denial of service for users of the targeted target system, forcing those targeted systems to slow down or even crash, thereby denying service to genuine users or systems.
How Does a DDoS Attack Work?
Cybercriminals carry out DDoS attacks by gaining unauthorized control of a network of computers. With the help of specially designed malware, cybercriminals turn those computers, and other systems (such as IoT devices) into a bot (or zombie). A group of such bot systems is known as a botnet. Cybercriminals will remotely control the botnet to carry out DDoS attacks.
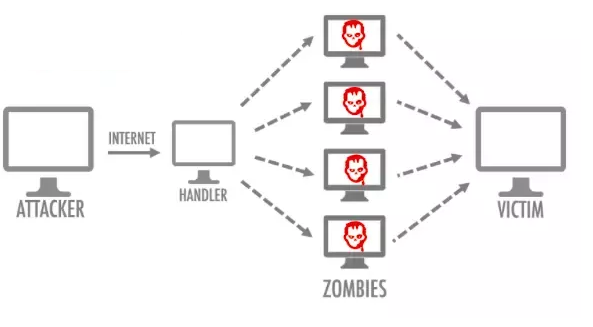
Cybercriminals can direct the devices in the botnet by sending instructions to each bot via a method of remote control. When the botnet targets the IP address of a victim (a website, server or other network resources), each bot will respond by sending repeated connection requests to the target, potentially causing the targeted machine to overflow capacity, resulting in a denial-of-service to normal traffic.
Botnets can be of any size; botnets with tens or hundreds of thousands of compromised machines have become increasingly common, and there are no upper limits to their size. Once a botnet is created, the attacker can use the traffic generated by those compromised devices to attack the targeted website or computer with overwhelming connection requests.
Types of DDoS Attacks
Below are some of the common DDoS attacks that attack web servers and web applications:
1. HTTP Flood
HTTP Flood is a type of DDoS attack that appears to be legitimate GET or POST requests that are exploited by a cybercriminal. This type of attack uses lesser bandwidth than other types of DDoS attacks, but it can force the server (target machine) to use maximum resources.
2. UDP Flood
A UDP flood type of attack targets random ports on a computer system or network with UDP (User Datagram Protocol) packets. It involves sending high volumes of UDP packets to the target machine.
3. SYN Flood
SYN Flood type of attack exploits vulnerabilities in the TCP connection sequence (in a server), known as a three-way handshake. The attacker sends repeated SYN requests (a TCP connection) to the target machine (server).
Usually, the server replies with an SYN-ACK response, and then the client system follows up with an ACK signal to establish the connection. In an SYN flood, the ACK is never sent. This leads to the build up of incomplete connections, leading to the server (target machine) slowing down or even crashing.
4. Ping of Death
Ping of Death is another type of DDoS attack which manipulates IP protocols by sending malicious pings to the target system. This method depends on the response by target machines. It can significantly increase bandwidth usage, eventually causing the server to slow down or crash.
5. Smurf Attack
Smurf Attack is another type of DDoS attack that uses a special kind of malware known as 'smurf' to exploit Internet Protocol (IP) and Internet Control Message Protocol (ICMP). In this type of attack, the targeted machines are flooded with spoofed ping messages-rendering the targeted machine unresponsive.
6. Application Level Attacks
Application Level Attacks exploit security vulnerabilities in the applications (targeted system's applications). The ultimate aim of this type of DDoS attack is not to target the entire server, but applications with known vulnerabilities.
7. Advanced Persistent DoS (APDoS)
Advanced Persistent DoS (APDoS) is another type of DDoS attack which is aimed at inflicting serious damage to the targeted machines. It uses a variety of attacks such as HTTP flooding, SYN flooding, etc., to attack the targeted devices. This type of DDoS attack can last for several days to weeks, mainly due to the ability of the attacker to change tactics at any moment and to create modifications to evade security defenses.
8. Zero Day DDoS Attacks
A Zero Day DDoS attack is another type of DDoS attack that is similar to zero-day cyber attacks. This type of attack exploits zero Day vulnerabilities (for which no patch is available) in the targeted systems.
DDoS Attacks: Prevention, Detection, and Mitigation
No matter the type of business you are running, keeping a business application or website up and running is critical to your brand's reputation and cybercriminals want to target this weakness with DDoS attacks. The unpredictability of DDoS attacks makes it difficult to take precautionary measures, which further incentivizes attackers to take action.
How can you protect your websites and web applications from such a cyber attack and stop DDoS attacks? As mentioned earlier, a DDoS attack will usually begin with a single compromised machine, but rather than exposing itself with a direct attack; it will locate other vulnerable systems and servers all over the world and secretly install the malware on them-creating a botnet.
The best way to prevent some types of DDoS attacks is by blocking unused ports, keeping the software up-to-date, and using modern networking hardware. Precautionary measures cannot avoid other types of DDoS attacks. In such scenarios, the best thing that you can do is to use malware or malicious activity detection software such as the Comodo cWatch to find the DDoS attacks early and prevent them from doing much damage to your business.
Comodo cWatch is one of the leading website security software that is available in the market today. cWatch can detect and remove web security threats (including DDoS attacks) and also enhances the speed of your website. With a powerful cloud-based malware scanning and 'Default Deny' approach, Comodo cWatch will go beyond your expectations.
You might have put in so much of your time and effort on your website (and your brand) or web application, so you need to be cautious when it comes to web security. Try cWatch today!
Related Resource

 (24 votes, average: 4.50 out of 5, rated)
(24 votes, average: 4.50 out of 5, rated)









