What is a (Distributed Denial of Service) Attack and How does it work?
A Distributed Denial of Service or DDoS attack is a very common type of cyber attack, and around 50 million DDoS attacks take place every year. Victims of the attack cannot access network resources and systems.
If you want to know how does a DDoS attack works imagine a street with an overload of traffic that it can’t handle. Attackers flood a network with an overload of traffic, and it cannot operate any more normally. It is challenging to stop such an attack, and systems with low-level security are vulnerable to DDoS attack tools and methods.
How does a DDoS Attack Work?
A DDoS attack tests the limit of a website or network by overflowing fake traffic to it. Sometimes attackers use short, repetitive requests on the site using an army of devices called a botnet. A botnet consists of malfunctioned devices, computers, or websites.
The botnet regularly attacks the target network and hinders its resources. This prevents users from accessing your website or slows down the site considerably. You may suffer substantial financial losses because of the decrease in performance and other resulting issues.
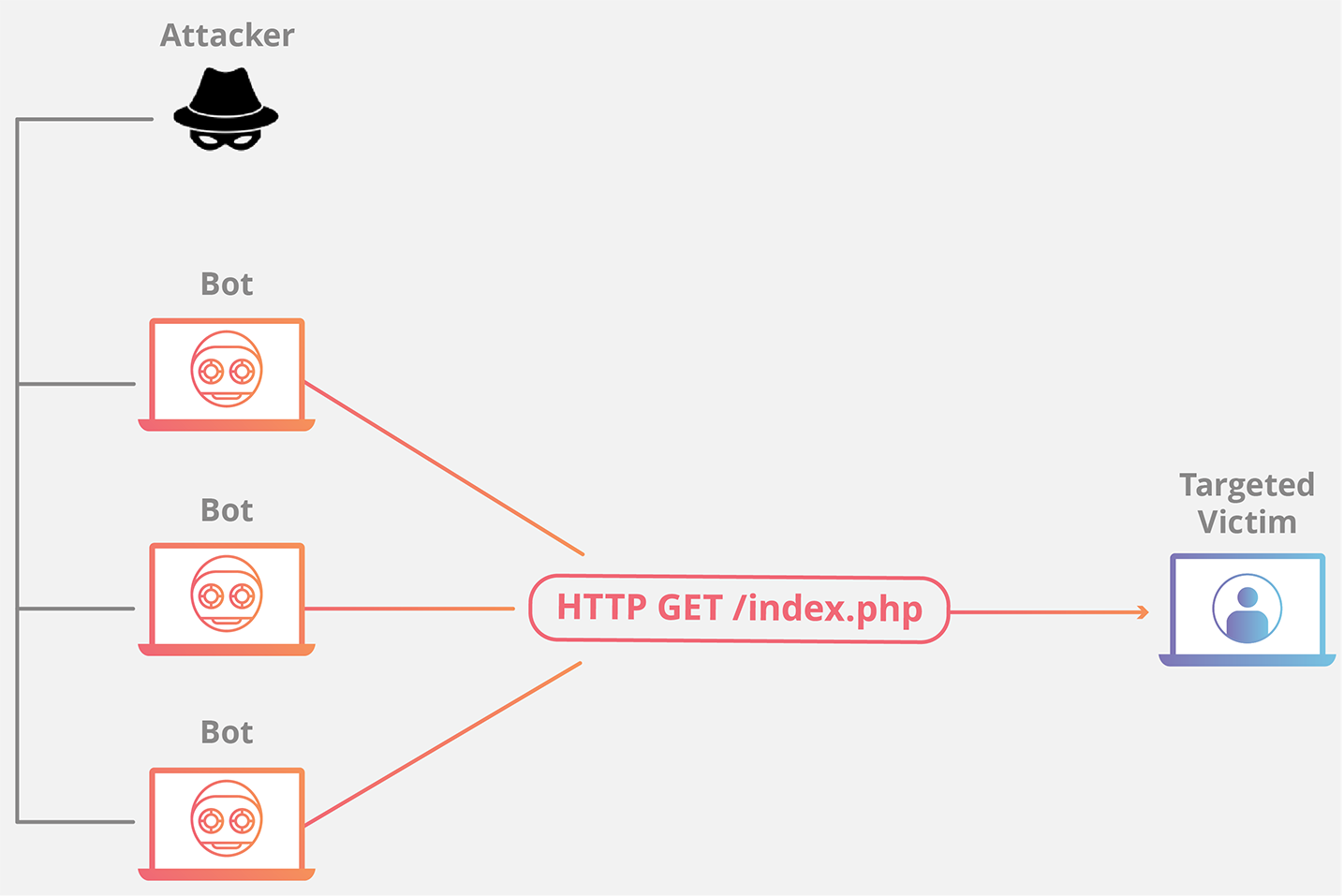
What happens in a DDoS attack?
A study of recent DDoS attacks shows that the attacked website gets slow and takes a lot of time to load due to the depletion of resources. Due to overload on the memory, CPU, or network, it is possible that the entire server may crash down.
Hackers make use of vulnerable internet of things (IoT) devices like smart TVs, security cameras, home lights, etc. to create a botnet. This botnet consisting of hacked devices then makes an overload of requests on a network which causes a DDoS attack and you should know about how does a DDoS attack works.
Types of DDoS Attack
Most of the DDoS attacks are made using a combination of IoT devices. As they can connect to servers and exchange data, it becomes easy to launch a DDoS attack using them. There are many different types of DDoS attacks.
1. Volume based DDoS attacks
This type of attack depends on the volume of traffic. It further includes:
- UDP Floods: User Datagram Protocol floods various ports of the network randomly that forces the server to show an ICMP packet that generates errors to the IP address.
- ICMP Floods: Attackers use multiple source IPs to overload the server with malicious ICMP packets that exhausts the server and forces it to reboot.
2. Protocol based DDoS attacks
Protocol based attacks take advantage of any weakness in Layers 3 and 4 protocol stacks and are measured in packets per second. This type includes:
- SYN Flood: Attackers send SYN packets to the victim network until the memory is overloaded that causes the network to crash.
- Ping of Death: Attackers manipulate the IP protocols by sending dangerous links to a server that can result in a reboot or server crash.
3. Application layer attacks
Application layer attacks are the most famous DDoS attacks type and can also affect bandwidth and networks. These include:
- Layer 7 HTTP Flood Attack: This attack is made to overload some parts of a server. It looks like legitimate traffic and is hard to detect.
- Layer 7 HTTP Flood - Cache Bypass: It causes the most damage by using all of a site’s resources without being cached.
How to Protect Your Device from DDoS Attacks – (Prevention, Detection, and Mitigation)
Although it is difficult to detect a DDoS attack, it is not impossible to protect your website or devices from it. Follow these steps to ensure DDoS attack prevention
- Protect your IoT devices: Most of the IoT devices and smart gadgets come with default passwords and usernames. As soon as you buy such a product, the first thing you need to do is to build a strong password so that it becomes difficult to access your device
- Use a secure router: Search the internet or contact your Wifi router’s manufacturer to ensure that it is secured from cybercriminals. It is the main pathway to your network, and you need to make sure no one can breach it.
- Use reliable security solutions: You can install popular and robust security solutions like Kaspersky or McAfee on your devices to give them extra protection. This will save your devices from receiving malware and getting hacked.
Conclusion
As you can see, cyber thugs are increasingly making use of DDoS attacks to overload networks that can have a serious impact. The above guide features all the necessary information and tells A how does a DDoS attack work.
It is vital to be informed about these attacks and ensure proper security measures are in place to protect your website or devices from a lethal DDoS attack.





