What is Session Hijacking?
September 15, 2022 | By Admin
What is Session Hijacking and How to Prevent it & Different Ways Of Hijacking
In the computer world, a session refers to the temporary interaction between a user and the website. In other words, the in-between time of the log-in and log-off during the operation of an account is called a session.
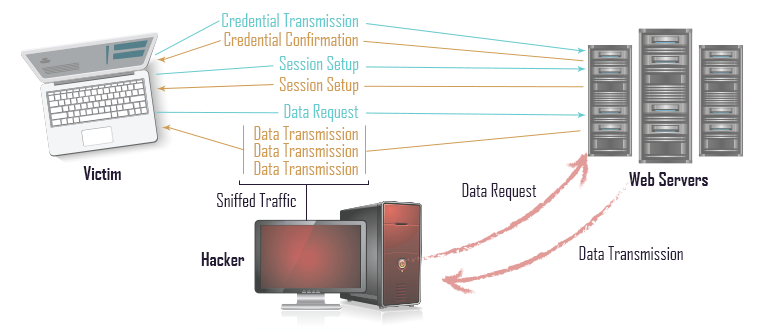
Session hijacking happens when online criminal places himself in between the computer and the website's server without revealing the identity to both endpoints and gains access to information by impersonating.
At this juncture, the intruder monitors and tries to capture everything from the online user's account. Sometimes, they take full control of the connection and even neutralize the legitimate user by denying them access to their own account.
During session hijacking, a hacker simply enters the server and accesses the info without the need to use a registered account. Besides these activities, the hacker may also make changes to the existing codes, modify server settings or install new programs that will support stealing valuable data and provide back-door entry whenever it is required.
How does Session Hijacking Works?
Technically, HTTP communication uses many TCP connections, thereby, it becomes mandatory for the server to recognize every user's connections with the help of a specific method. The most common one in use is the authentication process, once it is completed the server forwards a token to the client browser. The token is formed of a set of variable widths and it could be used in different ways – say like, in the header of HTTP requisition as a cookie, in other parts of the header of the HTTP request, in the body of the HTTP requisition or in the URL. The hacker exploits the session token by robbing or predicting a valid session token to gain unofficial access to the webserver. The session token compromising can happen in different ways.
In layman's terms, the hacker without revealing their true identity tactfully enters the conversation and gains access to key information which is being communicated. After taking control, the hacker has the ability to intercept, send and receive information without the knowledge of the sender and receiver. Session Hijacking happens in two ways and, they are:
Different Ways Of Session Hijacking
1. Session Sniffing
As mentioned above, the tokens help the hacker to intrude in a valid session. So, the online attacker first gets the session id. Sniffing is also known as Packet Sniffing is used to get the session id. When this is accomplished, the gains full unauthorized access to the webserver.
2. The Cross-Site Script Attack
For a hacker, the cross-site script attack is the best way to acquire a session-id without running any malicious codes or script from the client side. The victim is not targeted directly, however, the online fraudster compromises the weak points on the website and uses it to deliver a malicious script to the victim's browser.
How to Prevent Session Hijacking? - Session Hijacking Mitigation Tips
Usually, a session hijacking attacker steals the session id with the help of a malicious code on the client website. Thereby, it is essential to enable the protection from the client-side. Few preventive methods up ahead the road can help steer clear of all the dangers. Installing robust antivirus, anti-malware software, helps a lot, at the same time remember to keep the existing software up to date.
The latest technique makes use of an engine that fingerprints all requests of a session. Besides tracking the IP address and SSL session id, it also keeps a record of the HTTP headers. Any change in the header adds penalty points to the session and the session gets canceled when the points surpass a definite limit. Not worry, the limit can be configured. This is sufficient enough to tackle the situation because when the intrusion happens, it will have a different HTTP header order.
How cWatch Can Prevent Session Hijacking
Comodo cWatch delivers Managed Security Service to protect websites and its applications by integrating a Web Application Firewall (WAF) over a Secure Content Delivery Network (CDN). The Comodo Security Operations Center (CSOC) identifies threats and unknown files and analyses them and then performs the necessary actions. It provides continuous 24/7 website surveillance – an effective approach to prevent a range of website hacking attempts like session hijacking, session sniffing, and other suspicious threats from entering the websites.
It ensures real-time web traffic monitoring and incident identification and hence prevents session hijacking – where the hacker attempts to impose an attack through active computer sessions.
Related Resource
- Website Malware Removal
- What are Cookies
- WordPress Security
- Website Status
- Website Backup
- Check Website Safety
- Best CDN Price
- Cheap CDN
- Pay as You Go CDN
- CDN
- Free CDN
- Website Vulnerability Scanner
- Website Checker
- Website Security

 (21 votes, average: 4.52 out of 5)
(21 votes, average: 4.52 out of 5)









