What is SQL Injection (SQLI)?
October 13, 2022 | By Admin
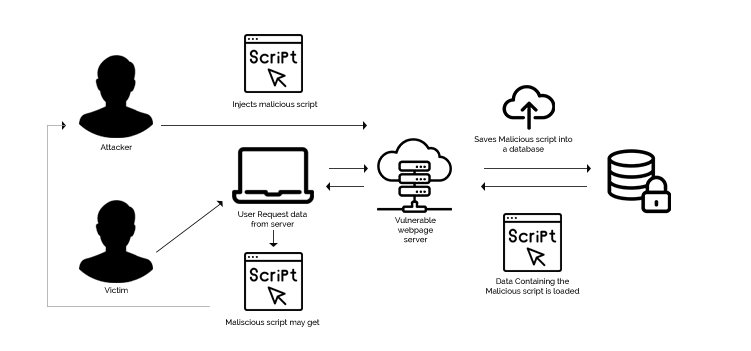
What is SQL Injection Attack?
SQL Injection (SQLI) is a backend database method used by hackers to take control of a web application by injecting malicious SQL codes. SQLI attacks are becoming very widespread because they are easy to do and require very little technical knowledge to perform. SQLI is a web application server issue that most developers are unaware of.
SQL Injection Types:
Hackers insert malicious SQL codes using different methods which include retrieving data in form of errors, conditions, and time. Let's take a detailed look at the SQL Injection types:
- Error Based SQL Injection
- SQL Injection Based on Boolean Errors
- SQL Injection is done through Time Based Query
1. Error Based SQL Injection:
In this method hackers can easily fetch details such as table names and content from visible database errors and this could be identified easily by hackers on the production servers. The best method here is to avoid displaying database error messages which in turn prevents hackers from fetching that information.
2. SQL Injection Based on Boolean Errors:
In a few cases, the error message is not displayed on a page when an SQL Query fails which makes it difficult for the hackers to gain entry into the vulnerable application. But there is still a way for hackers to find information. Whenever an SQL query fails some parts of the webpage seem to disappear or the whole website will fail to load.

On confirmation of these notifications the hacker inserts a false condition into the SQL query to test the vulnerability level of the application and the proximity of data extraction.
Example:
https://xyz.com/index.php?id=1+AND+1=1
After inserting this query if the website loads normally then it indicates that it is vulnerable to an SQL injection. To confirm this suspicion, the hacker would put a wrong query:
https://xyz.com/index.php?id=1+AND+1=2
As this condition is false and if the webpage does not work as usual it shows that the webpage is vulnerable to SQL Injection attack.
3. SQL Injection is done through Time Based Query:
In many cases, the Vulnerable SQL queries would be displayed visually on a web page but can be still easy to find out. Hackers here instruct the database to wait for a certain period before responding. If the site denies this and loads without any pause it means that they are not vulnerable. The SQL query implemented here would be similar to Boolean Attack but would have a sleep function in the query. For example, if the sleep time is 5 seconds then it instructs the database to sleep for 5 seconds.
Example Query:
https://xya.com/index.php?id=1+AND+IF(version()+LIKE+'8%',sleep(5),false)
Methods to Prevent SQL Query:
False SQL queries entry can be avoided by
Locating these SQL queries in a manual aspect would prove to be costly as there are chances of missing out. Hence, getting website security software is a good step.
Implementing web security software helps to validate this issue by having a thorough check on each and every query. Even if a vulnerable query is found it makes sure that the web page is loading properly by hiding the queries from the database.
- replacing special characters such as ( "", "%", "\", "_", "#").
- Stored procedures being used up in a database
- Use of prepaid statements in queries.
Related Resource
Vulnerability found in multiple stored xss form in wordpress version 1 2 5
How to Check if Your Site is Blacklisted
Website Backup
 (25 votes, average: 4.00 out of 5, rated)
(25 votes, average: 4.00 out of 5, rated)










