Vulnerability Found in Multiple Stored XSS Form in WordPress Version 1.2.5
May 08, 2020 | By Admin

On July 28, 2018, analysts in Comodo's cWatch Web Security team discovered a vulnerability in version 1.2.5 of the Wordpress 'Multiple Stored XSS Form', which may be used to steal user's personal data. This issue was caused due to improper sanitization, so the values were stored without proper validation or escaping.
While risks are common to any XSS, this vulnerability has stored XSS, most dangerous for users of Mondula Multi Step Form Plugin up to 1.2.5 on CDN for WordPress. Users concerned they have been exposed to this vulnerability should upgrade to the latest version of plugin.
More here:
https://www.owasp.org/index.php/Testing_for_Stored_Cross_site_scripting_(OTG-INPVAL-002)
Multi Step Form plugin has a drag and drop functionality enabled and a form builder that allow for quick and intuitive creation of nice-looking multi step forms. Forms can be embedded on any page or post with short codes. A remote attacker can exploit this issue by execute JavaScript code through Reflected XSS attacks.
Classification
Type: Improper Neutralization of Input During Web Page Generation ('Cross-site Scripting')
CWE: CWE-79
Proof of Concept
There are multiple stored and reflected XSS vulnerabilities in file class-mondula-multistep-forms-admin.php in fw_wizard_save action. The reason for this involves unsanitized user input from the following parameters:
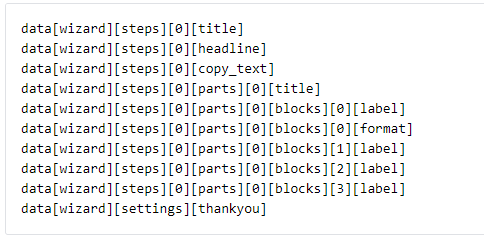
Exploiting this vulnerability requires authentication.
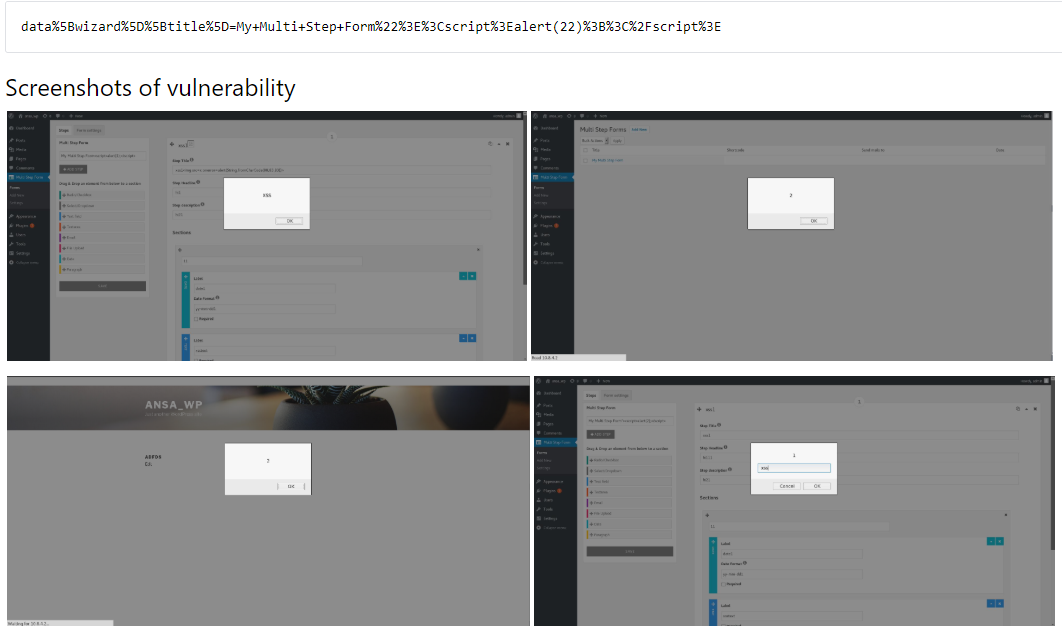
Example:
Locate Multi step form and enter payload and Save. The values are passed via Ajax → http://localhost/word496/wp-admin/admin-ajax.php
Code Difference
https://plugins.trac.wordpress.org/changeset?sfp_email=&sfph_mail=&reponame=&new=1919415%40multi-step-form&old=1917502%40multi-step-form&sfp_email=&sfph_mail=
In this case, sanitized values are missing, so the values were stored without proper validation or escaping. Sanitize affected vectors to avoid XSS. Corrected code shown below:
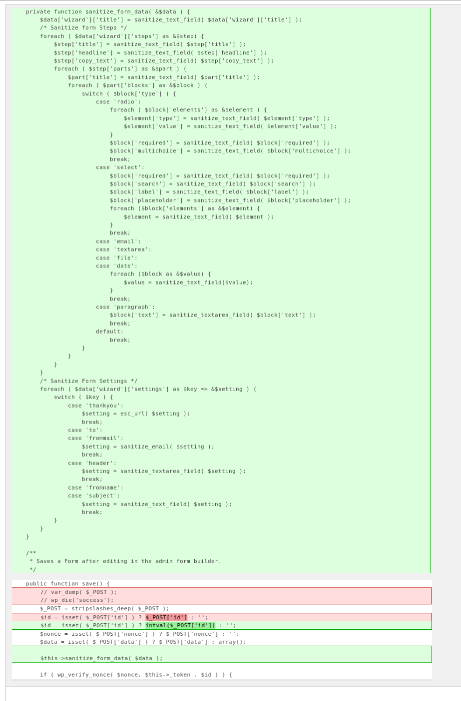
How to protect yourself (before patching):
Comodo Web Application Firewall (CWAF) provides powerful, real-time protection for web applications and websites running on Apache, LiteSpeed and Nginx on Linux. CWAF supports ModSecurity rules, providing advanced filtering, security and intrusion protection.
Why you need it:
- Protect sensitive customer data
- Meet PCI compliance requirements
- Block unauthorized access
- Prevent SQL injection and Cross Site Scripting (XSS) attacks

 (18 votes, average: 4.50 out of 5, rated)
(18 votes, average: 4.50 out of 5, rated)









