Infected WordPress Themes Still on WordPress.org
May 07, 2020 | By Admin

By Stas Goshko
Part 1:
FAKE SOCIAL.PNG CONTINUES TO RUN RAMPANT ON WORDPRESS THEMES
Having come across many exploits and vulnerabilities it is no surprise that Wordpress,
being one of the most common CMS used, seems to be a hacker favorite.
In order to stay proactive, we researched wordpress.org Apache Subversion (SVN) and discovered some major commonalities within some infected themes.
This presents a major concern as these infected files can be quite easily installed from the wordpress.org site directly.
During the next couple of blog posts we will publish a series of articles titled INFECTED WORDPRESS THEMES STILL ON WORPRESS.ORG, where we will share with you our findings in the hopes of helping stop the spread of these infections through awareness.
INFECTION OF FILES WITH IMAGES
The first set of deceiving files we identified were highly obfuscated code in some images. Within certain PHP scripts we noticed sets of false-image files that were a real serious threat.
Normally a user would think that their web antivirus scanner would detect this code but unfortunately many web malware antivirus' scans do not perform a file extension scan so that they can maximize their scanning speed.
The following is a list of the infected WordPress themes we have discovered:
- hxxps://themes.svn.wordpress.org/delish/1.2/social.png
- hxxps://themes.svn.wordpress.org/delish/1.3/social.png
- hxxps://themes.svn.wordpress.org/delish/1.3.1/social.png
- hxxps://themes.svn.wordpress.org/delish/1.3.2/social.png
- hxxps://themes.svn.wordpress.org/delish/1.3.3/social.png
- hxxps://themes.svn.wordpress.org/neworld/1.0.0.0.0.65565544254/images/social.png
- hxxps://themes.svn.wordpress.org/elgrande-shared-on-wplocker-com/1.1.0/images/social.png
After analyzing the specific content file "social.png" within these themes we discovered a 30kb highly obfuscated PHP code:
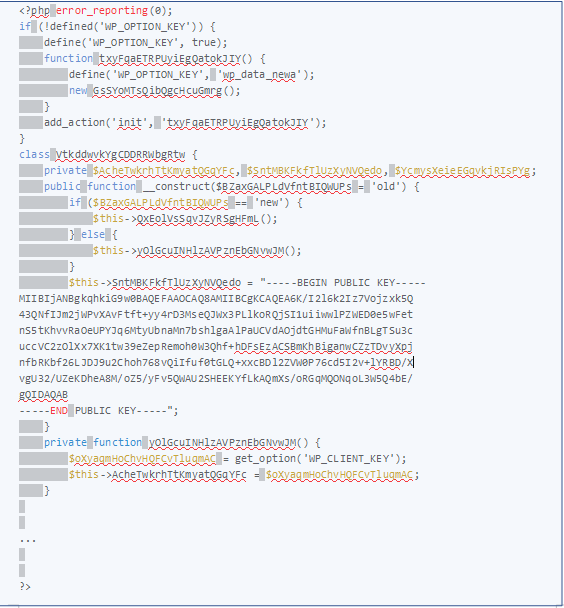
CONTINUED VULNERABILITY
Upon further investigation of this PHP code we identified it had included an RSA public key that, according to many infected users, this common malicious fake file is known as "social.png" has been running rampant for over 3 years, and yet many infected themes are still included in the wordpress.org repository.
Many websites infected with this malicious code caused their:
-
Server IP to be Blacklisted
-
Site to be broken when attempted to delete the files
-
Front page to display a blank page
Here this malware file was included encrypted domain list.
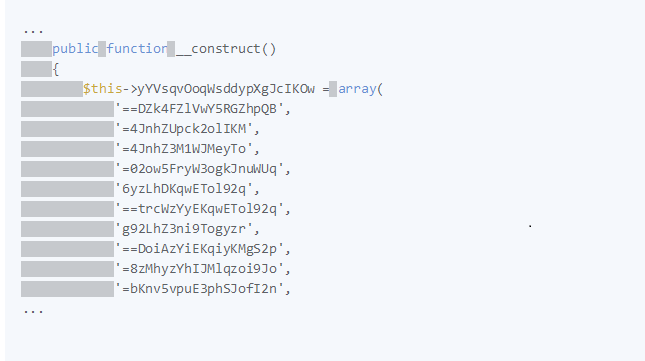
Yet after we decrypt the above we discover the following list:

And you guessed it, the attackers use the listed host sites to distribute malware and scum advertising. We continue to research and uncovered in Pastebin that someone provides a deobfuscated old version of this malware.
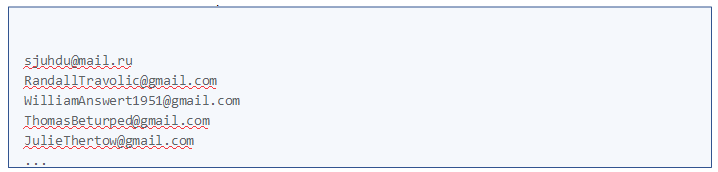
Yet in our version of the malware, we noticed that there was a list of encoded email addresses that were sending critical data about the infected system. After we decoded the list:
We found more variations of this malware that were using additional PHP obfuscator:
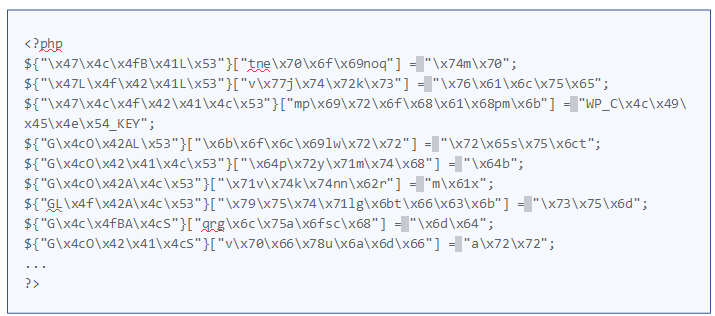
As well as a partially obfuscated version located here :
https://www.unphp.net/decode/5a92b78e37e1c7cbabf9e7dc00ac31c6/
CONCLUSION
Although this type of attack may not be common due to its complexity, it remains highly effective since it has targeted commonly used CDN for WordPress themes. Its effectiveness also lies in its multilayered approach that uses obfuscation, encryption, multiple domains and other forms of self-protection. enabling it is becoming increasingly difficult to detect through these advanced black hat techniques which hide their real purpose.
For individuals and organizations, dealing with this level of sophistication requires a multifaceted approach.
- Utilize a more complicated pre-moderation of plugins and themes on popular portals such as wordpress.org.
- Before implementing any themes and plugin, scan them with a reliable AV scanner. This will help to identify any malicious code.
- Back up your website before implementing any new code.
Ultimately the best way to mitigate this type of infection is to choose any third-party code wisely. In addition, having comprehensive cyber security knowledge remains critical in protecting websites and users alike. Having security analysts as a resource to inspect and investigate all code would be ideal. Connect with us if you are looking to have a security analyst on your side for less than a cup of coffee a day.
Related Resource

 (17 votes, average: 4.53 out of 5, rated)
(17 votes, average: 4.53 out of 5, rated)










