What is Hashing and How Does Hash Algorithm Works?
December 26, 2022 | By Admin
Hashing Definition: What is Hashing, Hash Techniques and Methods
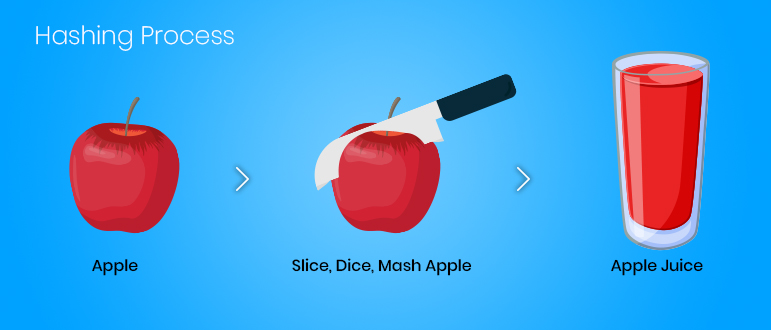
What is Hashing? - The hashing algorithm is referred to as the hash function: a term probably derived from the concept that the resulting hash value can be assumed as a "mixed up" version of the represented value.
Hashing refers to the transformation of a string of characters into a typically shorter fixed-length value or key that represents the original string. Hashing is apt for indexing and retrieving items in a database as it takes less time to find the item using the shorter hashed key in comparison to the time taken while using the original value. Hashing is also employed in several encryption algorithms.
Different Hashing Techniques
Three basic methods of dealing with hash clashes are available. They are:
- Chaining
- Rehashing
- Separate chaining
1.Chaining
This hashing technique builds a link list of all items whose keys possess the same value. During a search, this sorted linked list is sequentially traversed from the desired key. It involves adding a link field to each table position. There are three types of chaining:
General Coalesced Hashing
This is the generalization of the standard coalesced chaining method. In this method, extra positions are added to the hash table that can be employed for listing the nodes at the time of collision.
Standard Coalesced Hashing
This is considered to be the simplest of all chaining methods. It brings down the average number of probes for an unsuccessful search. It also executes the deletion without causing any negative impact on efficiency.
Varied Insertion Coalesced Hashing
This chaining type is the combination of general and standard coalesced hashing. In this method, the colliding item is inserted into the list instantly following the hash position unless the list developing from that position contains a cellar element.
2.Rehashing
This hashing technique deals with using a secondary hash function. The rehash function is successively applied until an empty position is identified in the table where an item can be inserted. The rehash function is again used to locate the item if the item's hash position is found to be occupied during the search.
3.Separate Chaining
It is not possible to insert items more than the table size. In certain cases, space much more than required is allocated leading to space wastage. To handle these issues, a method called separate chaining is available for resolving clashes. This hashing technique maintains a separate link list for all records whose keys hash into a specific value. As part of this method, the items ending with a specific number are placed in a particular link list. The 10's and 100's are not taken into account. The pointer to the node points to the next node, and the pointer points to the NULL value in instances when there are no more nodes. A few key benefits of this separate chaining method include:
The list items don't have to be contiguous storage
It permits traversal of items in hash key order
Need not worry about filling up the table whatever be the number of items.
What is Salting?
This concept of salting typically relates to password hashing. It is basically a unique value that can be added to the end of the password to develop a different hash value. This indeed adds a layer of security to the hashing process, particularly against brute force attacks. A brute force attack is one in which a computer or botnet attempts every possible combination of numbers and letters until the password is discovered. Furthermore, when salting, the extra value is referred to as salt. The concept here refers to the fact that by adding salt to the end of a password and then hashing it, you have actually complicated the password cracking process.
How cWatch can Provide Web Protection and Act as a Shield
When talking about layers of security, you can consider going in for cWatch web security, which is a security intelligence service capable of protecting networks and web applications from a variety of threats.
cWatch runs consistent malware scans on your domains and automatically removes any malware if detected. The Content Delivery Network (CDN) service enhances site performance by delivering your web content from the data center that is closest to your visitor.
The cWatch service regularly logs events on your domains to detect new attack vectors. These logs permit the Comodo Cyber-Security Operations Center (CSOC) to dynamically create and apply firewall rules to combat the most recent threats.
The console dashboard immediately tells you about the health of your sites, including any security-related incidents and attacks. cWatch is also capable of sending threat notifications to your email, phone number or SMS.
The Comodo Web Application Firewall (WAF) provides military-grade defense against SQL injections, bot traffic, hackers, and more. It is also possible for you to develop your own custom firewall rules.
With cWatch, you can run consistent scans every week for the top 10 OWASP threats and for known WordPress vulnerabilities.
cWatch helps identify malware, provides the methods and tools to remove it, and prevents future malware attacks
Comodo cWatch is powered by an advanced analytics-driven Security Information and Event Management (SIEM) process that can examine event data in real-time providing security intelligence for early detection of breaches and threats, log management, rapid incident response times, and compliance reporting.


 (23 votes, average: 3.83 out of 5, rated)
(23 votes, average: 3.83 out of 5, rated)









