CSRF Token And CSRF Attack
October 11, 2022 | By Admin
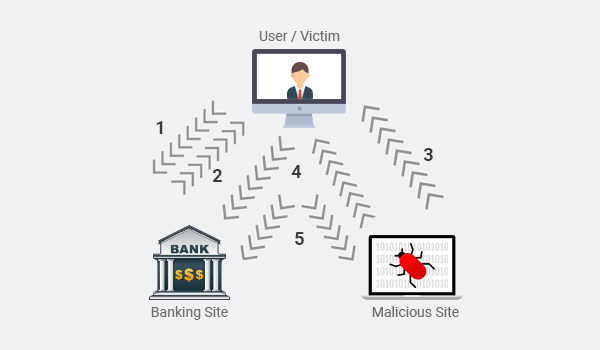
What is CSRF Attack?
Cross-site Request Forgery (CSRF), XSRF, or Sea surf is an attack on authenticated web applications using Cookies that tricks an end user to execute unwanted actions of the attacker's choosing. The attack is especially aimed at state-changing requests, not theft of data because the attacker will not see the response to the forged request. In another sense, the CSRF attacker exploits the liability of a web application that it has with the victim's browser. To accomplish this, a little help from social engineering like sending a link via email or chat is used. In the case of an administrative account, CSRF can compromise the entire web application.
What is CSRF Token?
In order to stay safe from Cross-site Request Forgery (CSRF) attacks, make use of the suggested and the most widely used prevention techniques which are known as an anti-CSRF tokens, also sometimes referred to as synchronizer tokens.
It is vital to include in the request the anti-CSRF token whenever a user is trying to raise any authenticated request or submit a form that might involve cookies. By doing so, the web application will then confirm the existence and correctness of this token before processing the request. If the token is incorrect or missing, the request can be rejected with ease.
Besides, it is equally important to use an existing, well-tested and secure anti-CSRF library. Based on the framework and language of your choice, many high-quality open-source libraries are ready-to-use.
A well designed anti-CSRF system includes the following characteristics:
. Each user session should possess a unique anti-CSRF token
. After the preferred amount of time, the session should expire automatically
. The anti-CSRF token needs to be cryptographically of random value with significant length and be secure.
It should be generated by a strong Pseudo-Random Number Generator (PRNG) algorithm.
. The anti-CSRF token is included as a secret field in the forms or within URLs
. The server will deny the requested action if the anti-CSRF token declines in the validation stage.
The CSRF Attacks
The CSRF attacks can be cannot be identified immediately but can happen only based on these below mentioned three points.
. The Web developers didn't take security seriously
. They opted out of the anti-CSRF token deliberately or by mistake
. The anti-CSRF token was implemented incorrectly
The CSRF Prevention
How to Prevent CSRF Attack?Numerous methods exist for CSRF attack mitigation and prevention. From a user's viewpoint, prevention is the element of safeguarding login credentials and rejecting illegal participants from accessing the applications.
The Industry Good Practices Include:
. Properly logging out from web applications when not in use
. Safeguarding usernames and passwords
. Avoiding web browsers from remembering passwords
. Avoiding accessing an application and browsing at the same time
In the case of some web applications, few solutions exist to prevent malicious traffic and block attacks. The widely used mitigation methods are to generate unique random tokens for every session. Subsequently, the session request is compared, reviewed, and verified by the server. The session requests with duplicate tokens or missing values are blocked. On the other hand, a request that doesn't match the session ID token is prevented from reaching an application.
Besides, double submission of cookies is another well-known method to block CSRF. This involves using unique and random tokens that are distributed to both the cookie and the request parameter. The server grants access to the application after verifying these tokens.
Comodo cWatch
The Comodo cWatch is a Complete Website Security Software Solution which discovers and continuously monitors all web applications. It also includes malware scanning, detection and removal services to enable organizations to take a proactive approach to protect their businesses and brand reputation from cyber-attacks. For more details visit our official page!
Related Resource
Cheap Content Delivery Network
Five reasons why small businesses are prone to malware attacks

 (20 votes, average: 4.20 out of 5, rated)
(20 votes, average: 4.20 out of 5, rated)









