SQL Injection Test Site
SQL Injection (SQLi) is one of the most common attacks in cyberspace. SQL Injection (SQLi) refers to an injection attack wherein an attacker can execute malicious SQL statements (also commonly referred to as a malicious payload) that control a web application’s database server (also commonly referred to as a Relational Database Management System – RDBMS). Any weakly secured website or web application that makes use of an SQL-based database can experience SQL Injection vulnerability. This is one of the most popular and oldest types of vulnerability. Also, it's one of the most dangerous website application vulnerabilities.
How to Test for SQL Injection Vulnerabilities?
When a hacker considers doing an SQL Injection attack, he/she can use it to bypass web application authentication and authorization mechanisms. It can totally give him/her the chance to retrieve the contents of an entire database. This online SQL injection can also do adding, modifying, and deleting records in a database – affecting data integrity.
If I'll thoroughly analyze the abilities of an SQLi attack, it can certainly give the hacker unauthorized access to sensitive data such as customer data, personally identifiable information (PII), trade secrets, intellectual property, and much other sensitive information. It's really horrifying how this information can be used against me.
How SQL Injection Happens
A database server is a requirement in order for malicious SQL queries to run. The hacker must initially find an input within the web application that is included inside of an SQL query. In order for an online SQL injection attack to take place, the SQL vulnerable sites need to straightaway include user input within an SQL statement. The hacker can then insert a payload that will be included as part of the SQL query and run against the database server.

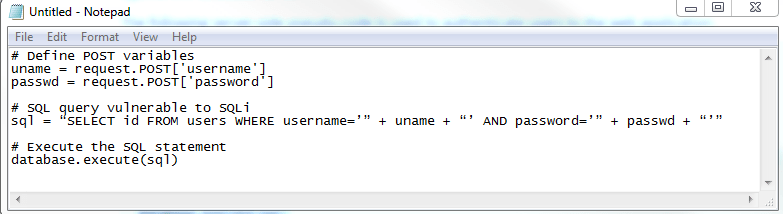
As I cite examples, the script above is a simple example of authenticating a user with a username and a password against a database with a table named users, and a username and password column.
A simple example of an SQL Injection payload could be something as simple as setting the password field to password' OR 1=1.
This would result in the following SQL query being run against the database server.
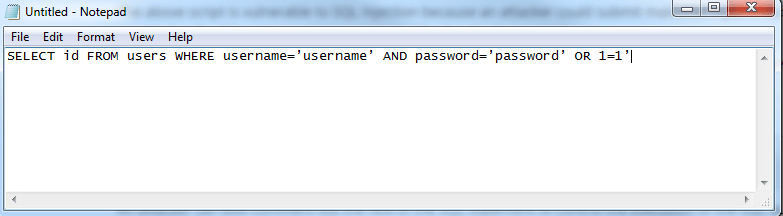
The hacker is also capable to comment out the rest of the SQL statement to control the execution of the SQL query further.
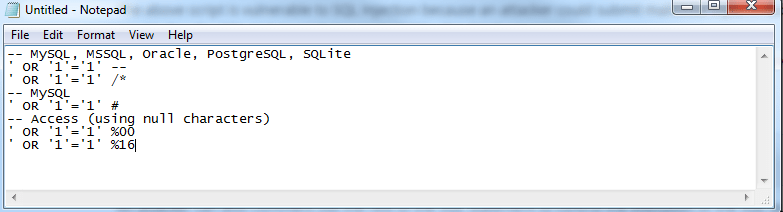
Once the query executes, the effect is returned to the application to be processed. This can result in an authentication bypass. In the event of authentication bypass is possible, the application will most probably log the hacker in with the first account from the query result. Then, the first account in a database is usually of an administrative user.
The Worst Things a Hacker can do with SQL
Structured Query Language (SQL) is a standardized programming language used for managing relational databases and performing various operations on the data in them. It is at first created in the 1970s. SQL is regularly used by database administrators, as well as by developers writing data integration scripts and data analysts looking to establish and SQL injection test analytical queries.
I should always remind you that when considering the following, it’s easier to understand how profitable a successful SQL Injection attack can be for an attacker.
- The hacker can utilize SQL Injection to deviate authentication or even impersonate specific users.
- One of SQL’s primary functions is to select data based on a query and output the result of that query. An SQL Injection vulnerability could permit the complete disclosure of data located on a database server.
- Since web applications utilize SQL to alter data within a database, the hacker could use SQL Injection to change data stored in a database. Changing data affects data integrity and could cause repudiation issues, for instance, issues such as voiding transactions, altering balances, and other records.
- SQL is used to take away records from a database. The hacker could use an SQL Injection vulnerability to delete data from a database. Even if an appropriate backup strategy is employed, deletion of data could affect an application’s accessibility until the database is restored.
- Some database servers are configured (intended or otherwise) to allow arbitrary execution of operating system commands on the database server. Given the right conditions, the hacker could use SQL Injection as the initial vector in an attack of an interior network that stands behind a firewall.
Some Important Things to Remember - Why use SQL Injection Test?
In this blog, I aim to teach that security is important just like everything else. There are many ways to practice cyber protection and business all at the same time. I just suggest you allot enough time and patience in studying the changing technology for efficient change. This attack is a valid point to check my website security.





