How to Prevent DDoS Attack against a DNS server?
DNS DDoS Protection — DNS flood is a type of DDoS (Distributed Denial of Service) attack in which the hacker targets more than one DNS (Domain Name System) server belonging to a particular zone and attempts to hamper the resolution of the resource records.
DNS servers are considered as the “roadmap” of the Internet, which helps the requesters to find the server they need. A DNS zone is a small portion of the domain name space in the particular Domain Name System (DNS). For every type of zone, administrative responsibility is assigned to a specific cluster of a server.
In a DNS flood attack, the attacker tries to overbear a particular DNS server using valid traffic, and by impeding the server’s ability and using the server resources to direct the legitimate requests to the zone resources.
Attack Description
DNS flood attacks must be differentiated from the several DNS amplification attacks. This is an unbalanced DDoS attack in which the invader sends a small query with the wrong target IP, which makes the target the beneficiary of much bigger DNS responses.
The attacker’s goal with these attacks is to flood the network by constantly exhausting the bandwidth capacity.
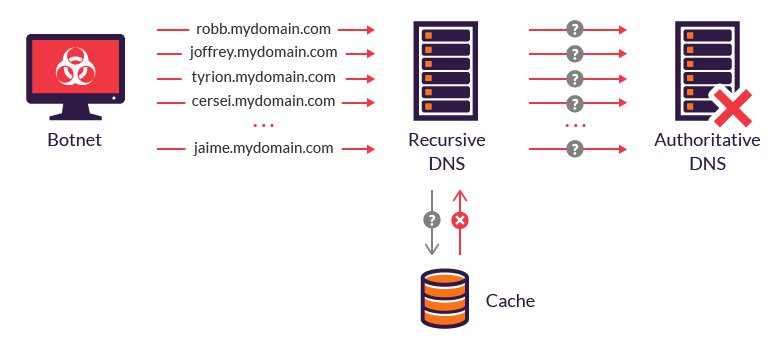
DNS floods are consistent DDoS attacks. The purpose of these types of attacks is to exhaust the server-side assets (such as memory or CPU) by a flood of UDP requests, which is created by scripts running on different compromised botnet machines.
A DNS flood attack is considered a type of UDP flood attack, as the DNS servers rely on the UDP protocol for the name resolution, known as the Layer 7 attack. With the UDP based issues, an entire circuit is never established; therefore, spoofing can be easily accomplished.
To attack a DNS server using a DNS flood, the attacker has to run a script, which generally comes from several servers. All of these scripts send malware packets using the wrong IP addresses. Layer 7 attacks do not require any response to be effective, and the hacker can easily send packets that are neither correctly formatted nor even accurate.
The attacker can easily spoof all the essential information, including source IP address, and make it appear that the attack is coming from different sources. The randomized packet data helps the offenders to prevent common DNS DDoS protection mechanisms, such as IP filtering, which is entirely useless.
The other common type of DNS flood attack is called the DNS NXDOMAIN flood attack, in which the hacker usually floods the DNS server with specific requests for records that are invalid or non-existent. The DNS server expands all of its resources to look for the records, like the cache files with bad requests, which has no resource to serve the legitimate requests.
How you can defend your server against DDoS attacks
The main objectives of DDoS systems are:
- Ensure infrastructure and services stay up and running.
- Ensure the availability of the services for legitimate users.
Always remember that, if objective No. 1 is not accomplished, then there is no advantage of object No. 2 because both the objectives are equally important.
Good DNS DDoS protection systems also reduce both false negatives and false positives. False negatives can cause a real attack to be missed, and false positives always result in legitimate users being blocked.
In most DDoS defense systems, traffic shaping is implemented. It includes clamping traffic to defend the service from falling over.
This type of strategy is filled with collateral damage, as the traffic filters are indiscriminately disposed of traffic. It means that the legit users are also thrown out alongside the malicious traffic.
To prevent this from happening, a DDoS defense system should be able to differentiate between illegitimate and legitimate users. This can be accomplished by implementing mitigation strategies and multi-modal detection, including DDoS threat intelligence, ZAPR (zero-day attack recognition,) and mitigation escalation.
All the strategies must be focused and fall under the Source Policy Violation. These strategies can sometimes be the most technically complex. Remember that the RFC Check lacks technical complexity, and Destination Protection has a significant impact on legitimate users.
The other strategy is to identify the pattern of the attacking user’s traffic by creating a filter and blocking the DDoS traffic with no manual intervention and advanced configuration. Also, this approach is called ZAPR, and can:
- Automatically create a custom filter to block the attacks with surgical precision quickly.
- Identify attack vectors, or common methods, of malicious traffic.
- Analyze incoming traffic.
Conclusion
DDoS attacks can be harmful, and it is in your hands to protect your DNS server from such attacks. So, please read the article and know in detail about these attacks and how to protect your server from them.
How to Protect WordPress Site from Malware





