SQL Injection Attacks (SQLi) and How to Prevent It
Initially, the creation of websites was simple as there was no JavaScript, no CSS, and a few images. But as the web gained popularity on the planet, there was a surge in demand for dynamic websites and advanced technology. In this post, we will talk about what is SQL Injection, its types, and its prevention.
Advance technology led to the development of CGI and server-side languages like PHP, ASP, and JSP. Innovated websites started to store user credentials and site content in databases. Therefore, it is easy to calculate that every popular server-side scripting language added support for SQL databases.
What is an SQL injection attack?
An SQL injection is also known as SQLI, is one of the most dangerous issues for data confidentiality and security in web applications. It includes the insertion of an SQL query through input data from the client to the application available on the internet.
It is a technique of code injection, which is used to attach data-driven applications. In it, malicious SQL statements are injected into an entry field for injection. A successful SQLI attack can provide access data to sensitive data, such as credit or debit card details, user passwords, or personal user information.
Many high-profile data breaches in recent times have been the result of SQL injection attacks. It leads to reputational damage and regulatory fines on the company.
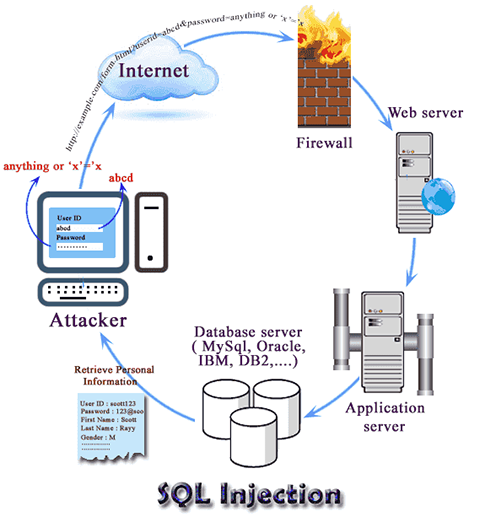
3 Types of SQL Injections Attacks
Basically, SQL injection types fall under the three categories, which also include sub-categories. We can also categorize SQL injection types based on the methods they used to access data and their damage potential.
1. In-band SQLI
An attacker always uses the same channel to communicate to inject an attack and to gather the result. It is the simplest and efficient way of SQL injection. There are two subcategories of this method:

- Union-Based SQLI
- Error-Based SQLI
This technique enjoys the advantage of the UNION SQL operator, which fuses many select statements produced by the database to get an HTTP response. This response may contain confidential data that can be leveraged by the attacker.
This SQL, attacker carries out actions that cause the database to produce error messages. These error messages provide information about the structure of the database to the attacker.
2.Inferential SQLI
It is also known as Blind SQLI, as the data is not transferred from the database to the attacker, and he is unable to see the information. He sends data payloads to the server of a web-based application. He observes the behavior and response of the server to learn about its structure.
These injections depend on the response and behavioral pattern of the server. They are slower to implement but can be harmful to the website. There are two types of Blind SQLI:
Boolean
An attacker sends an SQL query to the server prompting the application to return a result. The true or false query can produce varying results. The attacker will work out if the message generated a true or false result.
Time-Based
Hacker sends a query to the server, which makes the database wait before it can react. Whether a query is true or false, the attacker can see the time the database takes to respond. Based on the result, an HTTP response will be generated after a period of time. Then, the hacker can work out if the message returned true or false.
3. Out-of-Band SQLI
The hacker can only implement this form of attack when specific features are enabled on the database. This attack is mostly used as an alternative to the in-band and inferential SQLI techniques.
This attack is performed when the hacker is unable to use the same channel to implement the attack and gather information. These techniques depend on the capacity of the server to produce DNS or HTTP requests to transfer data to the hacker.
How to Prevent SQL Injection Attacks?
There are various effective ways to prevent SQLI attacks and to get protection against them. The initial step is input validation, which is a process of writing code that can identify unauthorized user inputs.
Input validation is known as the best practice, but it is not a foolproof solution to the threat. Because most of the time, it cannot map out all illegal and legal inputs.
For effective protection against SQL and other threats, a Web Application Firewall (WAF) is commonly used by professionals. It consists of a large updated list of meticulously crafted signatures that allows it to knock out malicious SQL queries.
cWatch comes under the most reputable companies that watch the security of web-based applications and also act as malware removal.





