How to DDoS?
DDoS attack stands for Distributed denial-of-Service attack is one of the most deadly and powerful weapons on the internet. Generally, an attacker can bring down a website by using the DDoS method. In this type of attack, the attacker makes a computer or website unavailable by flooding the site with huge traffic that can’t be handled by any system or server.
Usually, Distributed denial-of-service attacks make the online stores or services inoperable by sending massive traffic that can consist of fake packets, incoming messages, or requests of connections. In most cases, the bad guys carry out a small DDoS attack and threaten the website owners for ransom; otherwise, they can crash the online store or the services. In the most recent case that occurred in 2015, a group of criminals named Armanda Collective extorted web host providers, website owners, banks, and others in the same way.
Types of DDoS Attack
Network Layer Attack
In a network layer attack, an attacker targets the infrastructure used to host a website and sends a huge amount of data to crash or destroy the site.
Application Layer Attack
Application layer attacks are more complex than network layer attacks. In this attack, you have to target the specific program or software that is used by the target website in day-to-day functions.
There are multiple ways to carry out a DDoS attack. Some methods are easy, while in others, you may face a headache in the process. But you should know that easier methods are not more powerful and effective than the other complex techniques. We are sharing some best ways in which you can DDoS someone. Check it out below.
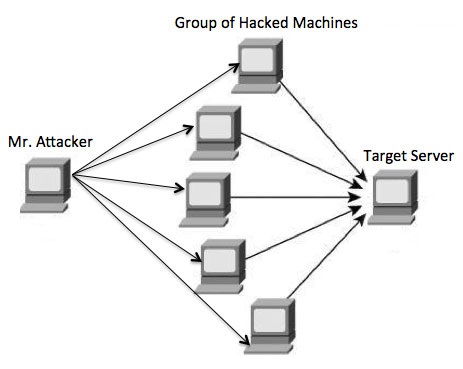
- Use Botnets
- Attack an IP using CMD
- A computer system. All you need to find out to attack the system is its Internet Protocol address.
- A wireless router can be attacked by using the ping of death method. A successful attack will prevent the router from providing internet to the connected devices.
A collection of internet-connected devices or computers is known as a Botnet. These are infected devices with malware and works on the instructions of a chief computer that is known as Command and Central center. The huge botnets consist of millions of computers, and most of the owners don’t even know that their devices have been compromised or under attack.
Many attackers use Botnets for carrying out various illegal activities like sending spam, cryptocurrency mining, hacking, etc. Some of the big botnets are available for rent through which you can make a DDoS, but keep in mind that you should be the highest bidder in the crowd to rent the service.
If you are unable to afford a botnet, you can use one of the most basic methods of carrying out a denial-of-service attack known as ‘ping of death.’ Through this method, you can flood an IP address with data packets by using CMD on your computer.
As it is a basic method and created on a small level, it would be best if you choose a small target such as-
How to Amplify a Denial-Service- Attack?
You can also enhance every data byte to amplify the attack by using a DNS or Domain Name System reflection attack. You can use the following steps to empower your attack-
- First of all, forge the IP address of the victim, and by using that forged identity, you can send out multiple DNS queries to an open DNS analyzer.
- The DNS analyzer starts processing each query and then transfers the information back to the attacked device. These information packets that are sent by the DNS analyzer are much bigger than the query is received from an attacker.
In the process of amplification of a DDoS attack, the query of 1 byte becomes 30 or 40 bytes or more in rare cases. You can also amplify the same process further by using a botnet through which you send packets of 100 gigabytes to the victim.
The Bottom Line - DDoS Attack Protection
The effectiveness or power of a distributed denial-service attack depends upon the methods that you are using to create it, such as the botnet is the most powerful way to creating this attack that can send the packets of 100 gigabytes while ping of death can be used only single devices. You should know the programming things before you proceed to create the DDoS and always make it by doing the complete homework on the target device or site.





