How to Protect Web Server from DDoS Attacks?
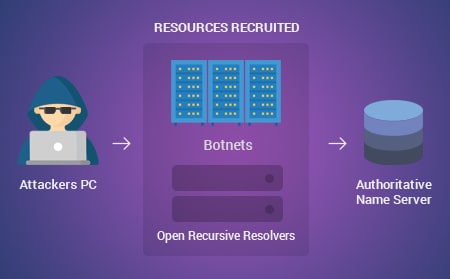
A Denial-of-Service (DoS) is an attack that denies legitimate users access to a resource such as accessing a network, website, emails, etc. or making it very slow. This attack is generally applied by hitting the target resource such as a web server with several requests simultaneously. Due to this, the server fails to respond to all the requests. This can lead to crashing of the servers or slowing them down. A Distributed Denial-of-Service (DDoS) is exedcuted by several compromised machines that target the same victim. This attack floods the network with data packets.
It is established that the concept of cutting off some business from the internet can lead to a major loss of business or money. The computer networks and the internet are responsible for powering a lot of businesses. A few organizations like e-commerce sites and payment gateways wholly depend on the internet to execute their business activities.
Types of DDoS Attacks on Web Servers
When such attacks are targeted at your web servers, they are capable of taking different forms:
- The first type of attack is made up of volumetric attacks that target the network leading to the web servers. These attacks send a huge volume of requests to clog the network stack or the network pipeline of the server. These could be TCP level SYN-Flood attacks or random page requests directed at your web servers.
- The volume type of attack targets the memory capacity of the web servers. The attackers execute this attack by sending specially crafted requests to the web servers that control the memory on the server and never release it.
- The third type of attack targets the processing power of your web servers by sending a huge of requests to particular pages that produce a heavy compute load on the web server, like login and search pages. The compute capacity on the server gets clogged but not the network.
Your business will experience a major loss in money if it depends on websites completely or even partially. If the attacker is just someone having fun, you are at their mercy if you do not have a response plan. If a ransom is demanded by the attackers, you could do a business calculation of ransom vis-a-vis lost revenue over time and either hold out for a while or pay.
How to Defend against DDoS Attacks?
Organizations that are keen on defending their web servers should search for a solution provider who understands web-based threats and web applications. A network layer solution is considered to be unsuccessful when safeguarding the web application layer. You will have to choose a solution that has complete insight into web traffic, not just IP addresses and ports. The potential to rate-control multiple sources or even an individual source should be a basic requirement.
The solution that is chosen should have the potential to discern malicious requests that attempt to overpower the network stack, compute or memory resources of the web server. It is good to have integrated IP reputation intelligence to block out requests from sources of bad reputation, but this could be complicated if the reputation principles are not regularly updated.
Firewalls: An Essential Part of any Server Configuration
Firewalls help in restricting or blocking access to every port except for those that should be publicly available. A firewall functions as an extra layer of protection even if your services themselves use security features or are restricted to the interfaces you would like them to run on.
Appropriately configured firewalls will be able to limit access to everything except the specific services you need to remain open. By exposing only a few pieces of software, you are actually reducing the attack surface of your server and restricting the components that are vulnerable to exploitation.
One such powerful Web Application Firewall (WAF) is available as part of the Comodo cWatch Web solution. This web security software is a managed security service capable of eliminating application vulnerabilities and protects web applications and websites against advanced attacks such SQL Injection, DDoS, and Cross-Site Scripting. The Comodo WAF comprises of the following security features:
-
Zero Day Immediate Response
Consistent updates of virtual patches for all websites under management and instant response to apply a patch for the zero day attacks when they become known to the public.
-
Stop Website Attacks and Hacks
Protects weak websites by detecting and removing malicious requests and preventing hacking attempts. This WAF also focuses on application targeting attacks, for example, WordPress and plugins, Drupal, Joomla etc.
-
Malicious Bot and Brute Force Prevention
Malicious bots and brute force attacks are blocked from websites. Provides protection of login pages and account registration forms from different attack vectors including protection from application denial of service, web scraping, and reconnaissance attacks.
-
DDoS Protection
Globally-distributed Anycast network enables effective distribution of traffic. It blocks all nonHTTP/HTTPS-based traffic, with a current network capacity in excess of 1 TB/s. Each PoP has multiple 100G and 10G ports, designed to scale and absorb extremely large attacks.
Key Web Security Features offered by the Comodo cWatch Web Security Stack
Besides the WAF, cWatch also provides other security features that include:
Cyber Security Operations Center (CSOC): A team of always-on certified cybersecurity professionals providing 24/7 surveillance and remediation services.
Security Information and Event Management (SIEM): Advanced intelligence that can leverage current events and data from 100M+ domains and 85M+ endpoints.
PCI Scanning: Enables service providers and merchants to stay in compliance with the Payment Card Industry Data Security Standard (PCI DSS).
Secure Content Delivery Network (CDN): A global system of distributed servers to improve the performance of websites and web applications.
Malware Monitoring and Remediation: Identifies malware, provides the methods and tools to remove it, and prevent future malware attacks.





