What is DNS and How Does DNS Work?
You will find yourself interacting with the largest distributed database in the world every time you visit a website. This large database is collectively called the Domain Name System (DNS). All the work carried out by the DNS happens so smoothly and instantly that you are usually completely unaware that it is even happening. The only time that you will get a glimmer about what the DNS is doing is when you are presented with an error after trying to visit a website.
This article that focuses on DNS address will take you through a brief discussion on Domain Names and Internet Protocol (IP) Addresses, DNS servers, and threats to DNS security. Finally, it will present a discussion on the security concerns for DNS servers.
Domain Names and IP Addresses
Domain names refer to the human-readable website addresses people use every day. For instance, google.com is Google’s domain name. In order to visit Google, you will just have to enter google.com into your web browser’s address bar. However, your computer does not understand where “google.com” is. Hence, the Internet and other networks use numerical IP addresses behind the scenes. One of the IP addresses used by Google.com is 172.217.0.142. If this number is typed into your web browser’s address bar, you will end up at Google’s website.
google.com is used instead of 172.217.0.142 because addresses like google.com are considered to be more meaningful and easier for people to remember. Despite the fact that IP addresses are known to change, the DNS servers are capable of keeping up with that new information. DNS is mostly treated as a phone book, where you search for someone’s name and the book supplies you with their phone number. DNS servers thus maintain a directory of domain names and translate them to IP addresses.
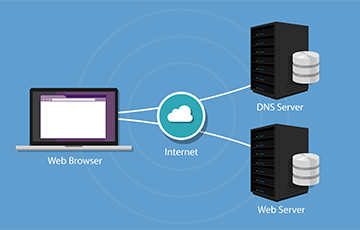
DNS Servers
DNS servers are responsible for matching domain names to their associated IP addresses. After typing a domain name into your browser, your computer will contact your current DNS server and ask what IP address is associated with the domain name. This is then followed by your computer getting connected to the IP address and retrieving the right web page for you.
The DNS servers you use are probably provided by your Internet service provider (ISP). If you are behind a router, your computer could be using the router itself as its DNS server, but the router forwards requests to your ISP’s DNS servers.
Computers cache DNS responses locally, hence the DNS request does not happen every single time you connect to a specific domain name that you have already visited. After your computer has determined the IP address linked with a domain name, it will remember that for a specific period of time, which boosts connection speed by skipping the DNS request phase.
Threats to DNS Security
Some of the biggest threats to DNS security include:
-
Distributed Denial of Service (DDoS)
Distributed denial of service (DDoS) is the most common DNS attack. During a DDoS attack, servers get flooded with traffic by the hacker, which indeed prevents authorized users from accessing the network. DNS servers cannot withstand that volume of capacity, and they quickly cease to be accessible.
-
SYN Floods
SYN floods are another type of Denial of Service attack. During such attacks, the hacker transmits "fake" data packages to invented destinations. However, the DNS servers fail to recognize that these requests are illegitimate. Hence, they will exhaust themselves by attempting to establish an active connection, resulting in them being unable to attend to real requests from users.
-
DNS Tunneling
During DNS tunneling, the data packets that are sent and then received over the DNS can actually become compromised. This DNS process is basically poorly monitored by a number of security systems, thus making it a tempting target. An increase in tunneling activity refers to the fact that a malware attack or data breach is in-progress.
-
Cache Poisoning
A DNS server becomes vulnerable to cache poisoning if it is badly configured. A cache poisoning attack takes website visitors to an infected server, which is actually controlled by the hacker. Very often, online users are not really aware that they are being phished, since the malicious website appears to be exactly like the original website.
-
DNS Hijacking
The targeted server’s Internet connection is taken over and reconfigured during DNS hijacking. This entire process is mostly administered by the use of malware. The hacker succeeds in redirecting online users to a different, malicious IP address.
All of these above-discussed threats can be prevented by installing a good web security software capable of performing multiple functions like virus detection and prevention, real-time edge protection for websites, incident management and response, blacklist repair etc. Here, we are talking about cWatch, a web security solution that offers you the following features:
- Malware Monitoring and Remediation: This feature allows cWatch to detect malware, provide the method and tools to remove it, and prevent future malware attacks
- Web Application Firewall (WAF): This WAF is a powerful, real-time edge protection for web applications and websites providing advanced security, filtering, and intrusion protection
- Security Information and Event Management (SIEM): Advanced intelligence capable of leveraging current events and data from 85M+ endpoints and 100M+ domains
- PCI Scanning: This scanning enables service providers and merchants to stay in compliance with PCI DSS
- Secure Content Delivery Network (CDN): A global system of distributed servers to enhance performance of websites and web applications
- Cyber Security Operations Center (CSOC): A team of always-on certified cybersecurity professionals providing 24x7x365 surveillance and remediation services
© 2026 Comodo Security Solutions, Inc





