The competition in a web environment is quite high. Although higher scalability and fast performance are indispensable for website owners, it's crucial to integrate a robust security strategy in the network system. Since the cyber threat landscape is evolving, it's necessary to secure a vulnerable website by detecting vulnerabilities and taking corrective measures to mitigate them. If these vulnerabilities are not fixed, hackers can have free access to the website with many privileges.
There are numerous approaches web developers and administrators can use to identify website vulnerabilities; one such way is to use a website vulnerability scanner. These scanners can give you an assessment report for determining the overall security posture of the website and also monitor new or changing vulnerabilities. Let's get to know how web vulnerability scanners can combat web-based cyber-attacks.
Detecting Vulnerabilities With A Web Vulnerability Scanner
Website vulnerability scanners are software designed to automate the search to detect security vulnerabilities in the website. When a website administration management is integrated with a website security scanner, it looks for vulnerabilities in web servers, web services, etc. Hence, a website vulnerability scanner is also known as a web vulnerability scanner or web app scanner.
The vulnerabilities of a website are mostly the loopholes in a web server through which cyber attackers can exploit web data. Here are some common vulnerabilities that a web app scanner can detect:
Cross-Site Scripting
Cross-site scripting is referred to as XSS. This kind of vulnerability is detected when the attacker injects malicious executable scripts into the code of a website or a web application. Attackers typically provide a malicious link to a user and urge them to click on it to start an XSS attack.

Cross-Site Request Forgery
Cross-site request forgery involves encouraging authenticated users to send a request to a website they are already authorized to. This vulnerability exploits a website's confidence it has in its authorized users.
Command Injection
OS command injection is a web security vulnerability that enables attackers to execute arbitrary operating system commands on the website server hosting the application and usually exploits the whole application and the site's data. This vulnerability can occur when the header information or user input has not been validated properly.
Distributed Denial Of Service
DDoS is an additional form or subclass of a DoS attack. This web vulnerability involves a range of connected online devices collectively known as a botnet. The botnet is used to overwhelm a target website by inducing fake traffic. While a DoS attack is made from one location to a single target, a DDoS attack is made from various locations simultaneously on a single target.
SQL Injection
SQL injection attack is a vulnerability where the code of websites and web applications gives attackers access to hijack the site's back-end processes. This allows them to extract and manipulate confidential information from the website databases. With this vulnerability, the attackers can take over the server completely.
Importance Of Conducting Web Vulnerability Scanning
Cyber attackers and malicious users of a website can easily take advantage of a website that doesn't use any security framework. They can steal data from the website, get access to confidential data, jeopardize a website user's identity, manipulate codes and much more. A website might be attacked thousands of times since, usually, half of the website visitors are a bot.
Such attacks can be successful if your website is not protected or scanned regularly. Security breaches can substantially affect the company's reputation and vulnerability to its revenue conduct. Thus, organizations managing web applications or websites should realize the importance of preventing such vulnerabilities.
Incorporating a website vulnerability scanner in the network can secure your system from malware and cyber attacks that can take over the entire server. Regular website vulnerability testing allows you to take certain measures to repair security weaknesses. This way, cyber attackers wouldn't successfully exploit the website data.
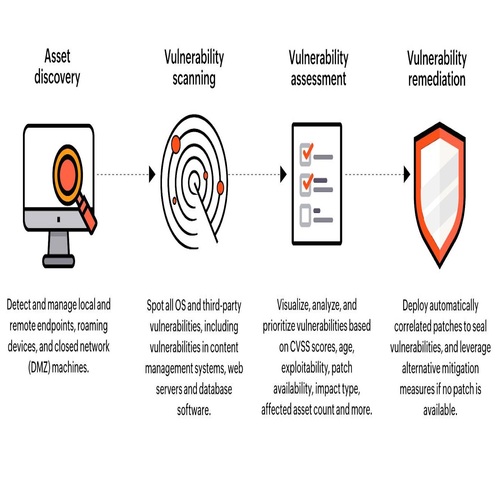
The Working Mechanism Of A Website Vulnerability Scanner
Website vulnerability scanning process can vary from one scanner to another. But commonly, their properties enable them to work in the following way:
- Once you have integrated the website scanner for detecting vulnerabilities in your network system, you can activate scanning from any of your browsing devices. The scanner would crawl throughout the website, every web page and find it.
- Once the crawling is completed, the scanning program will automatically detect all known web vulnerabilities.
- It identifies the vulnerabilities by performing pseudo-attacks and prepares an assessment report.
Safe coding methods are essential, but effective vulnerability assessments can assist organizations in strengthening their security posture by proactively detecting and closing security gaps. Thus, website vulnerability scanner tools can offer you the opportunity to rectify security weaknesses to ensure attackers can't detect and exploit them. Choose cWatch Web to add an extra layer of protection for your website security.





