Web users and businesses take on a lot of projects to do on open-source software. These open-source software can be an advantage in many ways that makes them great. You can use them free of cost. It is simple to alter or expand, and using OSS code helps speed up the development process of an app.
However, OSS comes with some major drawbacks, such as the vulnerability of obtaining security risks. Hence, it is essential to use an open-source vulnerability scanner when using open source. Read on to get valuable insights into how open-source security scans would work and how organizations should integrate vulnerability scanners into their security strategy. (Types of vulnerabilities assessed with open source vulnerability scanner)
Major Reasons To Use An Open Source Vulnerability Scanner
The principal reason for scanning open source is to cease security vulnerabilities that slip into your organizational network. Open-source codes might have a variety of security risks. Some functions in OSS might improperly validate input, giving leeway to cyber attackers to access sensitive information without authorization.
Additionally, there could be open-source modules with coding errors. Attackers can take advantage of it and access the application and even control the system hosting the application. Using an open source vulnerability scanner can potentially dissuade attackers and keep risks out of your network.
Although closed-source software has such drawbacks, they don't pose the risk of third-party developers reusing the code like OSS. Hence, organizations using open-source software created by third parties risk introducing security flaws into their codebases without realizing it.

An open-source project could virtually contain any kind of open-source security vulnerabilities. Licensing compliance is another factor to consider for using an open-source vulnerability scanner. Software developers may unintentionally utilize open-source code in various ways, which might be against the terms of the license regulating the code.
Using open-source codes in applications without realizing the origin of the code can result in licensing violations. Having open source vulnerability management in place of an organizational network system can protect against such risks. This enables you to find vulnerable codes in your open-source modules, libraries, and functions. If there is any potential licensing issue with open-source code that is essential for your organization's operations, it would be detected easily.
Risks Addressed By Open Source Vulnerability Scanner
A good open-source vulnerability scanner can address both vulnerabilities and license issues. Using a robust scanner would work holistically. The cost of buying a vulnerability scanner tool can depend on the number of IPs, applications and servers they scan. However, you can also opt for a free vulnerability scanner with the same capabilities.
The vulnerability scanner scans your software first to detect all the open source components in your code base. It would analyze the background and pedigree of the open-source software first to gain control and visibility over the risks. Next, the scanner would identify all open source licenses in the code base, checking their compatibility with the codes and compliance with the organizational policies determining whether they meet all attribution requirements.
Automating this scanning process can save you a lot of time, as open-source libraries have several dependents, each having various dependencies. You can lower legal compliance risks by legally abiding by all open-source licenses in your code base. The scanner can identify outdated open-source libraries and automatically recommend upgrading.
A reliable open source vulnerability scanner should have a feature for effective usage analysis. Such scanners would not only identify open source vulnerabilities, but they can also suggest a rectifying tactic for each vulnerability. The open source vulnerability scanner should detect your software's risky library with its vulnerabilities and evaluate whether the vulnerability is getting exploited in your software.
Integrating Open Source Vulnerability Scanner Into A Network
Deploying open source vulnerable management in the organizational security strategy can vary according to the tool. But the common set-up process involves:
- Purchasing the tool
- You can proceed with the set-up instruction if the tool needs to be hosted on-site. But if it is a SaaS solution, you can access it without setting it up yourself.
- Next, integrate the scanning tool with your software delivery workflow, which scans when open source is incorporated into a codebase. Enable the scanner to conduct scans against both source code and binaries, increasing your chances of finding security and licensing vulnerabilities.
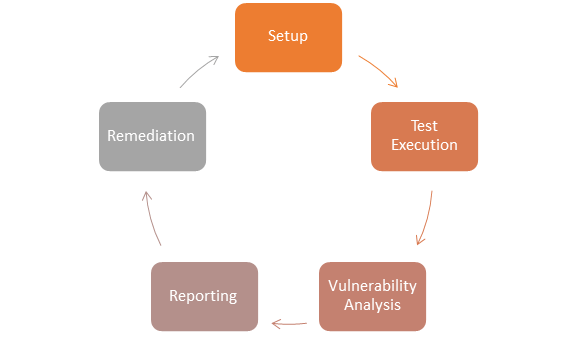
Many organizations try manually tracking open source licenses and potential security issues since it seems simple. But they quickly realize how impossible the task can be. Using an automated open source vulnerability scanner is the only method to take back control of your use of open source software for your project. If you are looking for robust scanning technology for protection against open-source risks, use cWatch for optimal security.





