What is Malware Removal?
In an era where digital threats are increasingly sophisticated, understanding and implementing effective malware removal strategies is crucial for maintaining the security and integrity of your digital assets. Malware, short for malicious software, encompasses a variety of harmful programs designed to infiltrate, damage, or turn off computers and computer systems. These include viruses, worms, trojan horses, spyware, adware, and ransomware. Malware removal, therefore, is the process of identifying, isolating, and eliminating these malicious entities from infected devices or networks.
The Importance of Malware Removal
The importance of malware removal cannot be overstated. Malware can lead to many problems, ranging from minor annoyances to severe security breaches. It can slow down or crash your systems, steal sensitive information, encrypt or delete crucial data, and even gain unauthorized access to network resources. This can translate to financial losses, legal liabilities, and reputational damage in business contexts. Thus, effective malware removal is a technical necessity and a critical component of any cybersecurity strategy.
How Malware Infects Systems
Understanding how malware infects systems is critical to effective removal. Malware can enter your system through various channels, such as email attachments, compromised websites, unsecured network connections, or installing infected software. Once inside, it can replicate, hide within legitimate programs, or modify system processes to avoid detection.
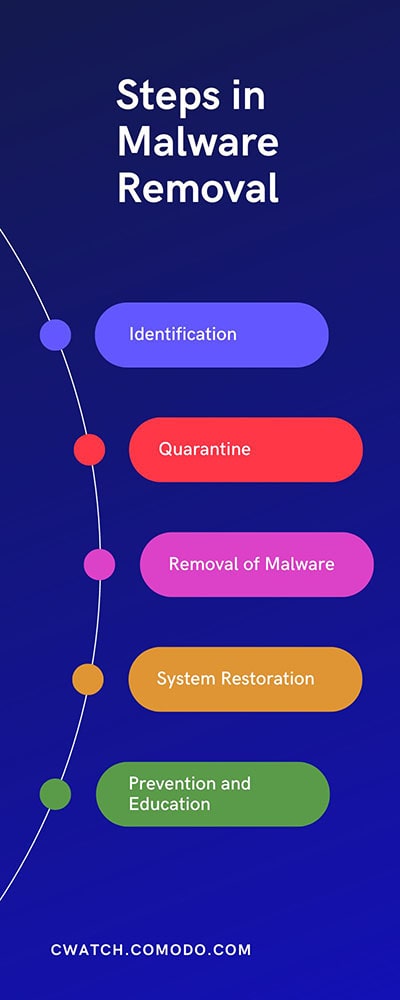
Steps in Malware Removal
The malware removal process typically involves several key steps:
- Identification: This involves recognizing the signs of a malware infection, including system slowdowns, unexpected pop-ups, frequent crashes, or unusual network activities.
- Quarantine: The affected systems should be isolated once potential malware is identified to prevent further spread.
- Use of Anti-malware Tools: Employ robust anti-malware software to scan and identify the malicious software. These tools are designed to detect a wide range of malware and are regularly updated to recognize the latest threats.
- Removal of Malware: The malware is removed or deleted from the system after identification. This can sometimes be complex, especially if the malware is deeply embedded within the system.
- System Restoration and Backup: If the malware has caused system damage, restoring the system to its original state might be necessary. This is where having regular backups becomes invaluable.
- Prevention and Education: The final step involves implementing strategies to prevent future infections. This includes educating users about safe computing practices, updating software and security tools, and monitoring systems for suspicious activities regularly.
The Role of Professional Malware Removal Services
Professional malware removal services, like those offered by Comodo cWatch, can be invaluable for individuals and organizations lacking the expertise or resources to manage malware threats effectively. These services provide both removal and proactive monitoring and defense mechanisms to guard against future threats.
Why Choose cWatch?
Choosing the right cybersecurity solution is paramount in the digital realm, where cyber threats loom large. cWatch by Comodo stands out as a beacon in this landscape, offering a suite of features and benefits that make it a top choice for businesses and individuals seeking robust malware protection. Here's why cWatch is the go-to choice for comprehensive digital security.
Advanced Technology and Expertise
cWatch leverages cutting-edge technology backed by Comodo's renowned cybersecurity expertise. With years of experience in the field, Comodo brings knowledge and innovation, ensuring cWatch users benefit from some of the most advanced security measures available.
Comprehensive Malware Protection
cWatch excels in providing complete malware protection. It's not just about removing existing threats; cWatch proactively monitors and defends against potential malware attacks, ensuring your systems remain secure against known and emerging threats. This proactive approach is crucial in a landscape where new malware variants constantly appear.
24/7 Monitoring and Support
One of the standout features of cWatch is its round-the-clock monitoring and support. Cyber threats don't adhere to a 9-to-5 schedule; they can strike anytime. cWatch understands this and provides continuous monitoring, coupled with an expert support team available 24/7 to address any concerns or incidents that may arise.
User-Friendly Interface
Despite its sophisticated backend, cWatch offers a user-friendly interface, making it accessible to users with varying technical expertise. This ease of use ensures that all users can effectively manage their cybersecurity without extensive training or technical knowledge.
Customizable Solutions
Recognizing that each organization has unique security needs, cWatch provides customizable solutions. Whether a small business or a large enterprise, cWatch can tailor its offerings to suit your requirements, ensuring you get the most effective protection for your specific environment.
Cost-Effectiveness
cWatch delivers high-quality cybersecurity solutions at a competitive price point. This cost-effectiveness is crucial for businesses, allowing them to secure their digital assets without straining their budgets.
Compliance and Trust
Comodo's cWatch helps businesses meet various compliance requirements, ensuring that they protect their data and adhere to industry standards and regulations. This compliance support fosters trust among customers and partners, who can be assured of the security measures in place.
Malware Removal FAQ
Answer: Malware, short for malicious software, is any software intentionally designed to cause damage to a computer, server, client, or computer network. This includes viruses, worms, Trojan horses, ransomware, spyware, and adware.
Answer: Common signs of malware infection include slower-than-usual computer performance, frequent crashes or freezes, unexpected pop-up ads, changes to your homepage or search engine, and unusual messages or programs that start automatically.
Answer: Yes, in most cases, malware can be removed entirely using various antivirus and anti-malware tools. However, some advanced malware may require professional intervention, especially if deeply embedded into the system.
Answer: A reputable antivirus or anti-malware program is generally safe and effective for primary infections. However, for more severe infections or if you're unsure about the process, it's advisable to seek assistance from a professional.
Answer: Preventing malware infections involves several best practices, including regularly updating your software and operating system, using strong, unique passwords, being cautious about email attachments and downloads, using a reputable antivirus program, and avoiding suspicious websites.
Answer: Yes, cWatch by Comodo offers comprehensive malware removal services. It helps remove existing malware from your systems and provides proactive monitoring and prevention tools to safeguard against future threats.






