What is Bot Protection?
The term "Bot Protection" has become increasingly significant in the ever-evolving digital landscape. Bots, short for robots, are automated programs that perform online tasks. While some bots are benign, aiding in tasks like indexing web content for search engines, many are maliciously designed to harm or exploit websites and online services.
Bot protection is a cybersecurity measure to identify and block these malicious bots. It serves as a crucial line of defense for websites, safeguarding them against various automated threats, including but not limited to web scraping, spamming, fraudulent transactions, and Distributed Denial of Service (DDoS) attacks.
These malicious activities can have a range of detrimental effects on a website or online service. For instance, web scraping can lead to stolen content or data, affecting a company's competitive edge. Spamming can undermine a website's integrity, leading to a poor user experience and potentially harming the site's search engine rankings. Fraudulent transactions and DDoS attacks, on the other hand, can cause direct financial losses and service disruptions, damaging a brand's reputation and customer trust.
Bot protection employs various techniques to differentiate between legitimate human and automated bot traffic. This differentiation is critical to ensuring genuine users have uninterrupted access while malicious bots are blocked or redirected. These techniques often include analyzing traffic patterns, checking for known bot signatures, implementing CAPTCHAs, and even using machine learning algorithms to detect and respond to evolving bot behaviors.
Furthermore, bot protection solutions are not just about blocking harmful traffic. They also play a crucial role in maintaining website performance. By filtering out unwanted bot traffic, these solutions help ensure that server resources are utilized efficiently, leading to faster load times and a better overall user experience.
In summary, bot protection is an essential aspect of modern cybersecurity strategies. It protects websites and online services from various automated threats, preserves the integrity of digital assets, and ensures a secure and seamless experience for legitimate users. As cyber threats continue to evolve, so will the methods and technologies employed in bot protection, making it a dynamic and critical field in internet security.
Best Practices for Bot Protection
In cybersecurity, adopting best practices for bot protection is crucial for ensuring the safety and integrity of digital assets. With the increasing sophistication of cyber threats, particularly those posed by malicious bots, organizations must employ a multi-layered approach to safeguard their online presence effectively. Here are some key strategies:
- Implement Advanced Bot Detection Techniques: Traditional methods, such as IP blocking and simple rate limiting, are often insufficient against modern bots. Instead, use advanced detection techniques that analyze behavior patterns, such as mouse movements and keystroke dynamics, to distinguish between human users and bots. Machine learning algorithms can also help identify and adapt to new bot tactics.
- Employ CAPTCHA Challenges: CAPTCHAs are practical tools for differentiating between humans and bots. Regularly update and vary CAPTCHA types (text-based, image-based, puzzle-solving) to prevent bots from learning and bypassing them. However, balance the difficulty level to ensure the user experience for legitimate visitors is smooth.
- Monitor and Analyze Traffic: Monitor website traffic to identify unusual patterns or spikes that could indicate bot activity. Analyzing traffic not only helps identify potential threats but also aids in understanding how bots are evolving and planning future defense strategies accordingly.
- Use a Web Application Firewall (WAF): A robust WAF can act as a gatekeeper for your site, filtering out malicious bot traffic based on predefined or dynamic rules. Ensure your WAF is regularly updated to defend against the latest bot signatures and attack vectors.
- Rate Limiting and Throttling: Implement rate limiting to restrict user requests within a specific timeframe. This can help mitigate DDoS attacks and reduce the effectiveness of brute-force attacks.
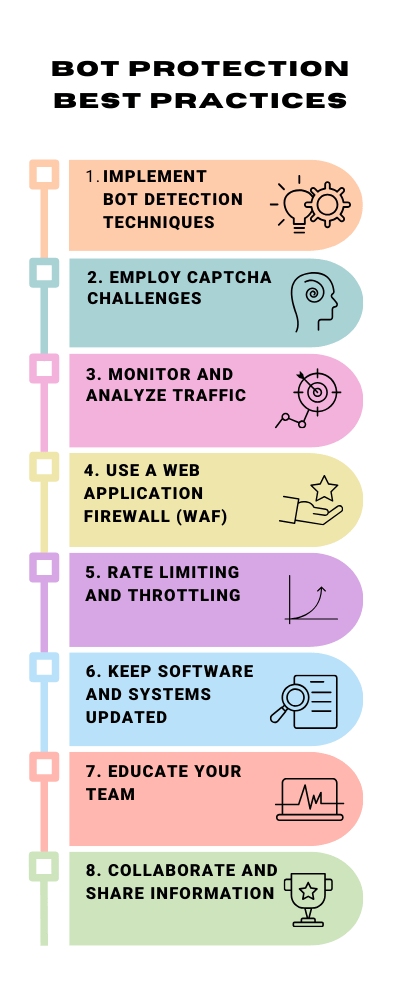
- Keep Software and Systems Updated: Regularly update all software, including content management systems (CMS), plugins, and server operating systems. Many bots exploit vulnerabilities in outdated software to gain unauthorized access.
- Educate Your Team: Awareness is a powerful tool in cybersecurity. Ensure your team knows the latest bot threats and the importance of following security protocols. Training staff to recognize signs of bot infiltration can aid in early detection and response.
- Collaborate and Share Information: Participate in cybersecurity forums and networks to stay informed about new types of bot attacks and defense strategies. Sharing information with peers can provide insights and help develop more effective protection mechanisms.
By incorporating these best practices, organizations can significantly enhance their bot protection measures, ensuring their digital ecosystem remains secure against the ever-changing landscape of cyber threats.
Why Choose cWatch for Bot Protection?
In the dynamic and challenging world of online security, selecting the exemplary bot protection service is critical. cWatch by Comodo stands out as a premier choice for several compelling reasons:
- Advanced Technology: cWatch leverages state-of-the-art technology to provide superior bot protection. Utilizing machine learning and advanced algorithms, cWatch effectively differentiates between harmful bot activity and legitimate user interactions, ensuring your website remains secure without compromising user experience.
- Comprehensive Security Solutions: cWatch offers a holistic approach to cybersecurity. Beyond bot protection, it provides a suite of services, including malware detection and removal, vulnerability scanning, and a robust Web Application Firewall (WAF). This comprehensive coverage means all aspects of your website's security are addressed under one roof.
- Real-time Monitoring and Response: With cWatch, your website is monitored around the clock. The system promptly detects suspicious activities and responds in real-time to neutralize threats. This proactive approach to security keeps your online presence safe at all times.
- Customizable Security Strategies: Recognizing that every website has unique security needs, cWatch offers customizable protection plans. Whether you run a small blog or a large e-commerce platform, cWatch tailors its solutions to your specific requirements, ensuring optimal protection.
- User-Friendly Interface: cWatch is designed with user experience in mind. Its dashboard is intuitive and easy to navigate, allowing you to manage your website's security effortlessly. Even those without technical expertise can easily understand and utilize cWatch's features.
- Expert Support: cWatch is backed by Comodo's security experts, who are available 24/7 to assist you. You can access top-notch support if you need help configuring your settings or responding to a security incident.
- Reputation and Reliability: Comodo, the powerhouse behind cWatch, is a renowned name in the cybersecurity industry. This reputation for reliability and excellence is a testament to the effectiveness of cWatch as a bot protection service.
- Cost-Effectiveness: Despite its advanced features and comprehensive coverage, cWatch offers its services at competitive prices. This cost-effectiveness makes it an accessible option for businesses of all sizes.
Choosing cWatch for bot protection means entrusting your online security to a leader in the field. With its advanced technology, comprehensive solutions, expert support, and user-friendly approach, cWatch is a prime choice for safeguarding your website against bot-related threats.
Bot Protection FAQ
Answer: Malicious bots are automated programs designed to carry out various harmful activities on the internet. These can range from scraping content and personal data from websites to launching DDoS attacks that disrupt service availability. For your website, this could mean compromised data security, reduced website performance, and a potentially tarnished brand reputation due to poor user experience or security breaches.
Answer: Bot protection systems employ various techniques to identify and block malicious bot traffic. This includes analyzing behavior patterns IP reputation, and using advanced algorithms to distinguish between legitimate human users and bots. Some systems also use CAPTCHAs or challenge-response tests to verify human users. Once identified, malicious bots are blocked or redirected, thus protecting your website from their harmful activities.
Answer: A well-implemented bot protection system minimizes the impact on legitimate users. While some methods, like CAPTCHAs, require user interaction, they are designed to be discreet and user-friendly. Advanced bot protection solutions focus on accurately distinguishing between humans and bots, ensuring that the browsing experience for real users remains seamless and uninterrupted. Regular updates and fine-tuning of the protection algorithms also help balance security and user experience.






